When people think of cybersecurity, most only think of defensive measures. This is unsurprising. Cybersecurity for personal devices is mainly defensive and it’s easy to assume that what works for personal will work for business. However, this isn’t true. Offensive tactics are also needed. So, let’s take a closer look at offensive vs. defensive cybersecurity.
| “Defensive tactics are strong, but it’s the proactive cybersecurity that truly keeps business networks secure.” – Tab Bradshaw, Chief Operating Officer, Redpoint Cybersecurity |
What is Offensive Cybersecurity?
Offensive cybersecurity preemptively identifies vulnerabilities and security weaknesses before an attacker exploits them. Offensive cybersecurity teams actively test the network’s defenses and provide valuable insights into an organization’s cybersecurity posture. Two of the most effective offensive cybersecurity approaches are threat hunting and penetration testing.
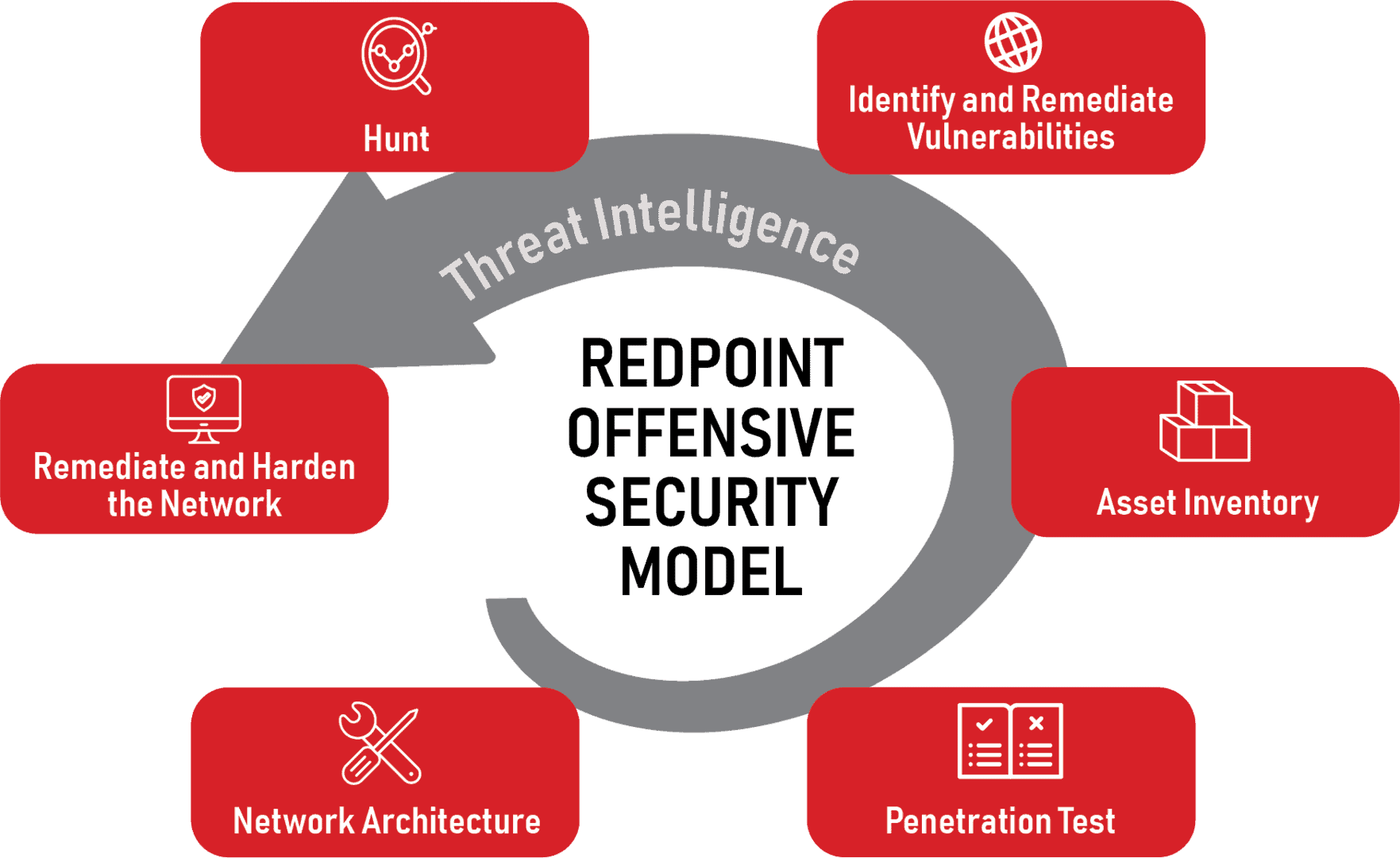
Various offensive cyber tactics have different processes, but generally an offensive cyber operation follows this model.
Network Architecture
The security team starts by mapping out the network’s architecture. This will help them understand the layout of all devices, servers, and connections within the network. Having this foundational knowledge is essential for planning and executing any cyber operation.
Test
Once they have a clear picture of the network, the team tests it for any potential weaknesses. This could involve penetration testing, adversary emulation, or simulated attacks to identify vulnerabilities. However it’s done, the goal is to pinpoint where the network might be susceptible to a real cyber attack.
Asset Inventory
The cyber offense team would also create an inventory of your digital assets. This includes hardware, software, data, and any other resources that are part of your network. This step helps them understand what’s at stake and where to focus protection efforts.
Identify & Remediate Vulnerabilities
After testing and asset inventory creation, detected vulnerabilities are recorded and remediated. Such vulnerabilities could be outdated software, misconfigured hardware, or weak security settings. How each is remediated will vary based on the type of vulnerability.
| Learn More About How You Can Keep Your Network Safe |
Hunt
Once the vulnerabilities are patched, the team actively hunts for any signs of intrusion or malicious activity that may have occurred before the vulnerabilities were detected. This involves looking for patterns or anomalies that could indicate a potential cyber threat.
Remediate & Harden Network
Should the team discover any threats during the hunt, they swiftly act to neutralize them. After that, they make the network stronger to prevent and mitigate future cyber attacks. They do this by setting up tougher security rules, improving system settings, and enhancing the network’s overall resilience.
What is Defensive Cybersecurity?
Defensive cybersecurity focuses on protecting information systems and networks from potential attacks. It involves the implementation of security measures and protocols to safeguard an organization’s digital assets. A good example of this would be a firewall.
Defensive operations typically go through the following process.
Risk Assessment
The first step in any cyber defense operation is to understand the risks. Risks would encompass where the organization is most vulnerable to an attack and what would be at stake if a breach occurred.
Policy Development
Based on the risk assessment, the security team develops policies to govern its cyber defense operations. These policies might cover everything from password requirements to procedures for responding to a detected threat.
Implementation
Next comes the actual implementation of security measures designed to protect the organization’s assets. This could include firewalls, intrusion detection systems, encryption, and other technical measures.
Monitoring
Once the security measures are in place, the team continuously monitors systems and networks for signs of a cyber attack. This is often done in tandem with automated tools that can notify professionals of suspicious activity 24×7.
Incident Response
If a potential threat is detected, the team needs to respond quickly to mitigate the threat. This is where pre-planned policies come into play. Everyone involved already knows exactly how to respond.
Recovery
After a threat has been mitigated, any affected systems or data must recover. This might involve restoring systems from backup, repairing damaged systems, or even rebuilding systems from scratch.
Review
Whenever an incident occurs, it’s important to review how it went so the team can respond more effectively in the future. Periodically, the entire process should also be reviewed so it keeps up with evolving threats.
Many small-and-medium-sized businesses only have defensive cybersecurity measures. While it’s important to keep your cyber defenses strong, offensive measures are also necessary for business-grade cyber protection. Understanding the scale and sophistication of cyber threats can be eye-opening, as highlighted in the Cybersecurity Tips for SMBs by CloudSecureTech, providing valuable lessons in cybersecurity.
Therefore, many larger business owners bring red-team cyber professionals aboard. Most SMBs would be wise to follow suit, especially since criminals rely on smaller businesses having fewer security measures.
What is The Red Team in Cybersecurity?
The red team is the offensive team in cybersecurity. They simulate attacks on an organization’s information system to scan for vulnerabilities and test the effectiveness of the organization’s security measures.
As mentioned, the best cybersecurity protocols involve both offensive and defensive cyber operations. For that reason, the red team is just one of many color-named teams found in cybersecurity. For instance, the blue team would be the people responsible for defensive cybersecurity.
Here’s a quick chart comparing these teams of cybersecurity experts. Please note that some individuals may cross-over in their roles.
Comparing Cybersecurity Professionals
| Red | The offensive team |
| Blue | The defensive team |
| Purple | Blends offensive and defensive tactics |
| Green | New professionals, main focus is to learn from other teams |
| Yellow | Responsible for developing and maintaining the organization’s security policies and procedures |
| Orange | Responsible for the development and improvement of the tools and technologies used by the other teams |
| Black | Similar to the red team but operates without the knowledge of the blue team. Their role is to simulate a real-world attack scenario where the defenders have no prior knowledge of the attack. |
| White | Typically oversees the entire cybersecurity operation |
Enhance Your Cybersecurity Posture With Redpoint’s Threat Mitigation Group
Redpoint’s Threat Mitigation Group keeps your organization secure through a unique approach to target, pursue, and eliminate threats on your network – we Hunt the Hunter™.
Composed of experts in both offensive and defensive cybersecurity strategies, we can partner with you to create a robust cybersecurity program and curate industry-specific threat intelligence to provide insight into the cyber threat landscape.
Alongside defensive and offensive security services, the Redpoint team also provides military-grade digital forensics, cloud security, and managed network security. When you partner with us, you’ll get an enterprise-grade, holistic cybersecurity solution without the enterprise price.
Contact us to find out more about how we can help you.