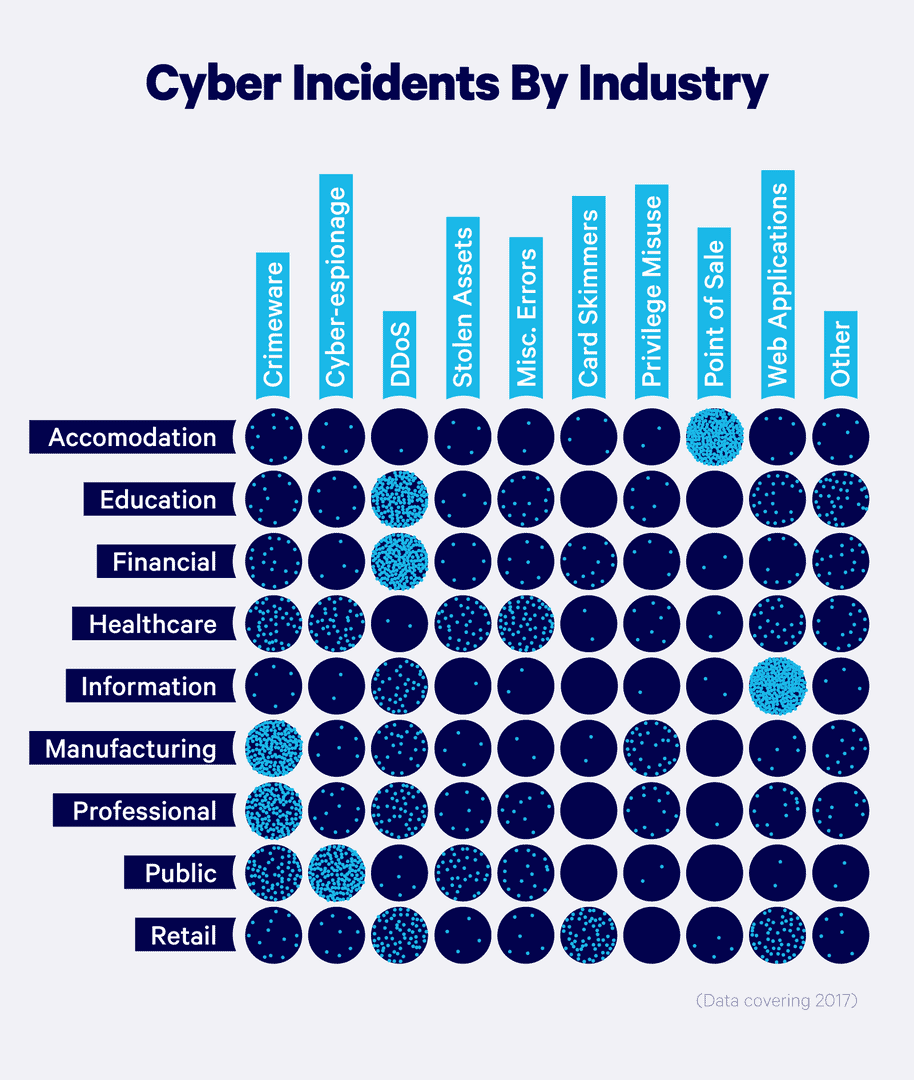
Duke University’s enormous cybersecurity survey found that 80% of American firms admit to having suffered cyber attacks. Small, mid-sized business, or enterprise, there’s no such thing as too small to be attacked or too big to be breached.
“No matter how sophisticated the cybersecurity framework, infrastructure is never entirely secure”, says Tab Bradshaw, Chief Operating Officer. “Having an actionable, effective plan to mitigate attacks is vitally important for any organization.”
Incident response is a vital component of an organization’s cybersecurity strategy. It’s the process that kicks into gear when a security breach occurs. With the average cost of a data breach reaching $9.44 million, having an effective incident response plan can mean the difference between a minor hiccup and a major catastrophe.
What is Incident Response?
Incident response definition: incident response is a structured approach to addressing and managing the aftermath of a security breach or cyberattack. The goal is to handle the situation in a way that limits damage, reduces recovery time and costs, and ensures that the organization’s reputation remains intact.
💡Incident Response Plans Offer Tangible ValueIBM found organizations with incident response teams and tested response plans have an average cost of data breach $2.66 million lower than those that do not. |
In an ideal world, an organization would have formalized incident response best practices and a plan in place, clearly outlining the processes and technologies to be used in identifying, containing, and resolving various types of cyberattacks.
A well-crafted plan can empower cybersecurity teams to swiftly detect and contain cyber threats, expedite the restoration of affected systems, and curtail the financial losses, regulatory penalties, and other expenses linked to these threats.
Phases of Incident Response
Understanding the incident response lifecycle is key to managing any cybersecurity incident effectively. The lifecycle typically includes the following stages:
- Preparation: Setting up an incident response team and creating a detailed incident response plan.
- Identification: Potential security incidents are detected and reported.
- Containment: Limit the scope and magnitude of the incident.
- Eradication: Finding and eliminating the root cause of the incident.
- Recovery: Restoring systems and operations back to normal.
- Lessons Learned: Reviewing what happened and how it was handled to better respond to future incidents.
Each stage plays a crucial role in ensuring that the incident is handled efficiently and effectively.
The Incident Response Team
Typically, an organization’s incident response efforts are guided by a computer security incident response team (CSIRT).
This team is made up of stakeholders from across the organization—the chief information security officer (CISO), security operations center (SOC) and IT staff, but also representatives from executive leadership, legal, human resources, regulatory compliance, and risk management.
An effective incident response team typically includes roles and responsibilities such as:
Incident Response Manager: Oversees the response to incidents, coordinates efforts among team members, and communicates with senior management.
Security Analyst: Investigates the incident, identifies the cause, and suggests remediation steps.
Forensic Analyst (DFIR): Conducts a forensic analysis to gather evidence and understand the incident’s details.
IT Coordinator: Ensures that all IT systems are ready to support the incident response process.
The Incident Response Process
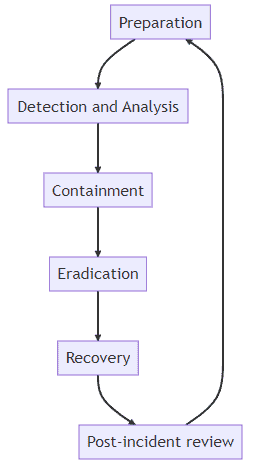
Most organizations follow the standard incident response frameworks developed by the SANS Institute, the National Institute of Standards and Technology (NIST), and the Cybersecurity and Infrastructure Agency (CISA) when dealing with security events.
The cyber incident response process typically involves the following stages:
1. Preparation
First, the Cyber Security Incident Response Team (CSIRT) conducts regular risk assessments to identify vulnerabilities in the network and potential threats. They prioritize the threats based on possible impact to the business. With this risk analysis, the CSIRT can update response plans or draft new ones as needed.
2. Detection and Analysis
Next is detection and analysis. The security operations team monitors for indicators of compromise and anomalies that may point to malicious activity. They analyze logs from devices and security tools, filtering out false positives and triaging actual alerts by priority.
3. Containment
Once a real threat is confirmed, containment begins. The goal here is stopping the threat’s spread and preventing further damage. The CSIRT isolates affected systems and locks down unaffected ones during incident response.
4. Eradication
After containment comes eradication. The team works to completely remove the threat from compromised systems and scans unaffected ones to ensure no remnants of the threat remain.
5. Recovery
When the CSIRT is confident the threat has been neutralized, recovery starts. This can involve patching, rebuilding from backup, and bringing remediated systems back online.
6. Post-Incident Review
Finally, there is a post-incident review. The CSIRT analyzes evidence to determine how the attack occurred, identify exploited vulnerabilities, and close those gaps to prevent recurrence. The goal is to ensure such incidents don’t occur in the future.
Technologies Involved in Incident Response
CSIRTs must also outline the security solutions that an organization’s incident response system should include. These technologies will impact the effectiveness of response, and can help automate workflows.
Security Information and Event Management (SIEM) systems are a critical component of effective incident response. SIEM solutions provide real-time analysis of security alerts generated across an organization’s infrastructure and applications. By aggregating and correlating log data from all IT systems and devices, SIEM enables security teams to identify attack patterns and anomalous activity that may indicate malicious compromise.
Endpoint Detection and Response (EDR) is another key technology for security incident response. EDR focuses on detecting, containing, and remediating threats on endpoints – a prime initial target for attackers. EDR continuously gathers data from endpoints to provide visibility into suspicious events and facilitate rapid response.
Network segmentation represents a key long-term containment strategy. By dividing the corporate network into smaller segments, organizations can limit the lateral movement of attackers and isolate sensitive systems and data. Effective segmentation restricts an attacker’s ability to pivot between network zones once an initial foothold is gained.
Maintaining resilient backup and recovery capabilities is also essential for mitigating cyber incidents. Backup tools create restore points that can be used to roll back data corruption or loss from attacks like ransomware. Capturing point-in-time copies also provides forensic evidence of the incident for analysis.
Patch management represents a critical recovery control for closing security gaps exploited in an incident. Deploying software updates and patches for known vulnerabilities across endpoints, servers, and network devices reduces the attack surface and prevents reinfection.
| More cybersecurity resources: |
Proven, Performant Incident Response Services
In the ever-evolving landscape of cybersecurity, understanding and implementing an effective incident response strategy is not just an option, but a necessity.
At Redpoint Cybersecurity, we are a team of former nation-state cyber operators with one mission: to help our clients and partners mitigate cyber threats. Our military-grade technologies and expert cyber professionals apply their knowledge of the attacker perspective to facilitate efficient, effective, and scalable responses to cyber breaches.
We understand that incident response is not a one-size-fits-all process. It requires a tailored approach, considering the unique needs and vulnerabilities of each organization.
Stay safe, stay prepared, and always be ready to respond with our team. Discuss your security needs with an experienced professional.